GeoPrivacy

Emerging ubiquitous applications generally imply the use of geo-located devices (e.g., cell-phones, vehicles) that are aware of their physical location. These objects are often personal devices, so learning their location usually implicitly discloses the location of their owner. Of the various sorts of personal data whose collection can be a threat to privacy, location information is one of the most sensitive: it can help to trace a person, to identify that person's interests or to detect an unusual behavior. It is thus crucial to protect the past, current and future locations of an individual from disclosure (except by explicit consent of the person concerned).
One of the approach we favor is to reduce location accuracy to reach an acceptable tradeoff between the utility of location-sensitive tasks and privacy protection. Some cryptographic techniques (e.g., secure multiparty computation) can also compute a global result depending on a large number of people without disclosing any information on particular individuals.
To this aim we develop a toolkit to evaluate the trade-off between location accuracy and privacy. In this toolkit, one can import new attacks algorithm and new sanitization techniques, in order to evaluate this trade-off.
PhD positions available (GeoPrivacy attacks, Architectural or Algorithmic approaches to geoprivacy protection). Send me an email.
We organize the APVP2011 Workshop which has a GeoPrivacy special track !
Mobility/Location Aware
Algorithms
Geographical awareness of user-carried devices combined with short-range wireless networking induces a fundamental shift in distributed system paradigms: contrary to the Internet model that abstracts away location, systems of mobile users are tightly coupled with the real geographic world.
This new characteristic of distributed systems is not taken into account in traditional computing models and toolboxes.
To provide a complete solution to deal with systems of interconnected mobile devices, we are working in two complementary directions: the definition of suitable computing models, and the definition and implementation of algorithmic building blocks for resilience in such systems.
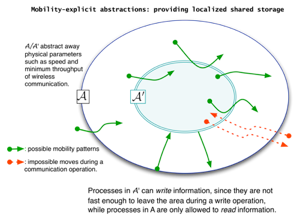
We are working on providing formal reasoning framework based on realistic and usable models that include user mobility, failures and connectivity. The interest of these mobility-explicit computing models is twofold: first, they serve as a basis to provide formal proofs of resilience algorithms, and second, they provide inputs for dependability evaluation in mobile systems.
The computational counterpart to such models is the provision of a toolbox to ease the programming of systems with explicit mobility. We are focusing on the definition of algorithmic building blocks such as storage, agreement and membership. These building blocks may be classified with respect to their primary goal: they either take advantage of mobility, e.g., by providing localized services [Roy et al. 2008], or aim to hide the intrinsic complexity of mobility from the programmer, by providing a classical distributed systems interface.
PhD positions available (Geocasting, Geocomputing, etc.). Send me an email.
Dependability evaluation in a mobile context
Recent advances in wireless and portable devices technologies have opened new opportunities for innovative services that can be accessed by mobile users in highly dynamic environments, through a combination of ad-hoc and infrastructure based communication networks. Such services cover a large variety of application domains including information and entertainment (voice and video streaming, online gaming, contextual information services, etc.), as well as safety and dependability critical services (hazard warning, safety and traffic management for transportation systems, assisted living support systems and healthcare monitoring, crisis management, etc.). This fast growing area poses some significant challenges from the dependability evaluation point of view. The main challenge concerns the quantification of dependability characteristics taking into account the combined effects of faults affecting the mobile nodes and their communication, and the mobility of these nodes. In particular, the development of quantitative assessment strategies with realistic mobility patterns and failure models is needed to provide a faithful validation of the quality of service provided by these applications.
Our research in this context covers two complementary evaluation approaches:
model-based evaluation using analytical and simulation techniques and
experimental measurements.
Model–based evaluation is well suited to support the comparative analysis of architectural solutions at the design stage based on the assessment of system level dependability properties such as reliability, availability and safety. Our contributions concern the development of modeling approaches that are well suited to master the complexity of the target systems and to capture the behavior of the system that results from the occurrence of failures and recovery actions and from the mobility of the users. The proposed models are based on generalized stochastic Petri nets (GSPNs) and Stochastic Activity Networks (SAN). Also, simulations have been performed to estimate some connectivity characteristics in dynamic mobile scenarios, in particular for vehicular applications. Three case studies have been investigated:
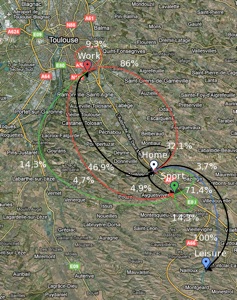
a) a distributed application using cooperative backups on mobile nodes [Courtes 2008, Courtes et al 2007] (Figure 1),
b) a replication service for applications running on ad-hoc networks [Matthiessen et al 2007], and c) an automated highway system based on platooning [Hamouda et al 2009b].
Another complementary approach that is particularly relevant to improve the accuracy of dependability assessments in mobile environments, concerns the development of experimental techniques based on laboratory testbeds (the ARUM platform) or on the analysis of data collected from real life systems. Such experiments can provide a realistic estimation of some parameters that are used in analytical models such as connectivity rates or specific failure rates that are pertinent in a mobile setting, along with their associated distributions. In particular, our research aims at developing new fault injection techniques to analyze the behavior of mobile systems in the presence of faults.
Two major difficulties need to be addressed: i) what new types of faults and failures are induced by mobility, and ii) how to inject faults in a mobile device or in a location-aware system. To address these difficulties, we recently began the development of a laboratory-scale platform to experimentally evaluate and validate resilience mechanisms of mobile ubiquitous systems (https://www.laas.fr/ARUM/wiki/) [Killijian et al 2008, Killijian et al 2009] (Figure 2). It scales the physical dimensions of a real-life mobile system into ones that are practical for experimentation in a laboratory environment. By changing scale, we plan to emulate systems of different sizes, from networks of communicating road vehicles, down to nanorobots injected into the blood systems to perform surgery. The platform will serve as the basis for the development of new fault injection tools and techniques.
This research has been partially carried out in the context of the HIDENETS European project “Highly Dependable ip-based Networks and Services”, the ReSIST European network of excellence “Resilience for Survivability in IST” (lien ), and the MOSAIC research project (Mobile System Availability, Integrity and Confidentiality) partially funded by the French national research program on Security and Informatics (ACI & SI).
For more details, you can check my Publications and/or send me an email.

Past interest
In my (numerous) previous lives, I worked on :
-
•Reflective middleware
-
•Portable Serialization
-
•Software adaptation
-
•Robotics faul-tolerant architectures with David Powell, Jérémie Guiochet, Félix Ingrand
For more details, you can check my Publications and/or send me an email.